ECDSA public key compression in Erlang
In this blog post, I will share an Erlang code snippet that can be used to compress the Elliptic Curve Digital Signature Algorithm (ECDSA) public keys. This technique can significantly reduce data size without compromising security.
Before diving into compression, it’s essential to grasp the structure of ECDSA public keys. These keys consist of two coordinates, commonly denoted as (x, y), representing points on an elliptic curve. Compression focuses on minimizing the size of these coordinates.
The process of compressing ECDSA public keys
1. Understand ECDSA Public Keys:
ECDSA public keys are represented by two coordinates, denoted as (x, y), which correspond to points on an elliptic curve.
2. Determine the Parity of y:
Calculate the parity (even or odd) of the y-coordinate.
- If y is even, a specific prefix byte 02 is set.
- If y is odd, a different prefix byte 03 is set.
3. Concatenate Prefix and x-coordinate:
Concatenate the chosen prefix byte with the x-coordinate. This creates a binary representation that combines the information about the parity of y and the x-coordinate.
4. Final Compressed Key:
The result of the concatenation is the compressed form of the ECDSA public key.
Erlang code snippet
Now, to implement this compression technique in Erlang, you can refer to the code snippet:
This code provides a practical implementation of the compression process discussed above.
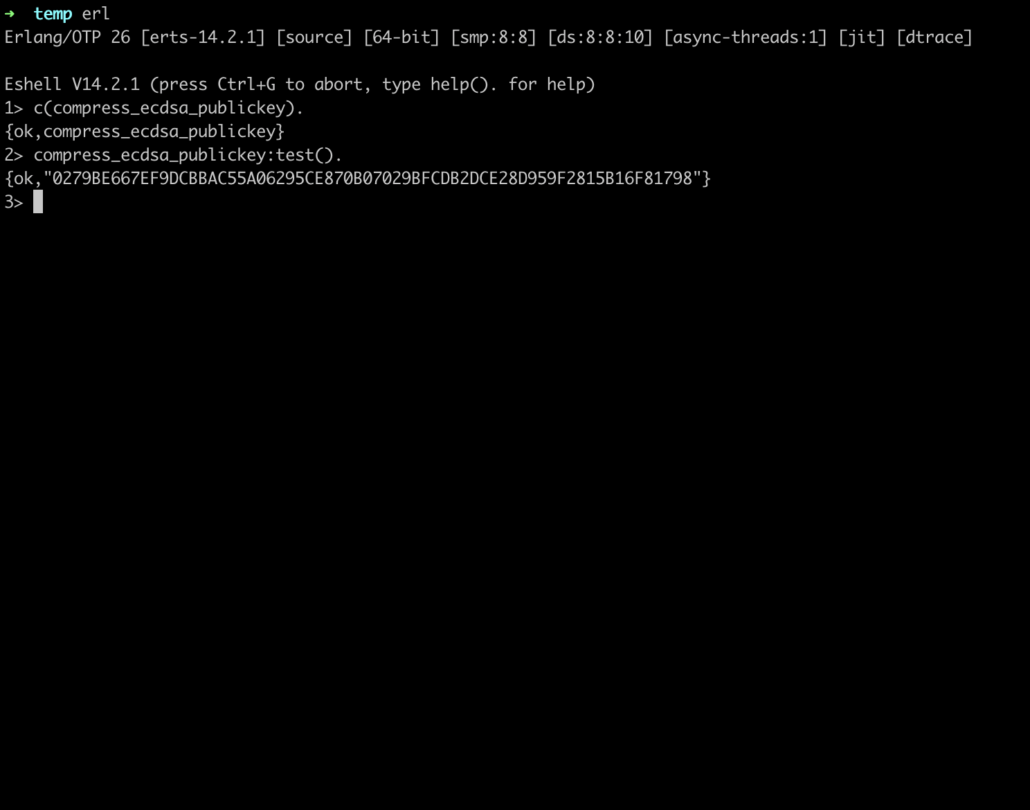
To run the provided code, you’ll need to follow these steps:
1. Save the code in a file with the name “compress_ecdsa_publickey.erl”. Make sure the file extension is “.erl”.
2. Open a terminal and navigate to the directory where you saved the file.
3. Start an Erlang shell by typing “erl” and pressing Enter.
4. Compile the module by running the following command inside the Erlang shell:
c(compress_ecdsa_publickey).
This will compile the Erlang module and generate a BEAM file (.beam).
5. After successful compilation, you can run the “test/0” function:
compress_ecdsa_publickey:test().
This will execute the “test/0” function, which in turn calls the “compress_ecdsa_publickey/1” function with a sample uncompressed public key. The result will be printed on the console.
Conclusion
In summary, the compression process involves choosing a prefix based on the parity of the y-coordinate and concatenating these components to form a compressed binary representation of the ECDSA public key. This technique reduces the size of the public key while maintaining its integrity for cryptographic purposes.


Leave a Reply
Want to join the discussion?Feel free to contribute!